Configuring Baculum¶
Access from web browser¶
Baculum API
Use these parameters to access the Baculum API:
Address: http://localhost:9096
First time login: admin
First time password: admin
Baculum Web
Use these parameters to access the Baculum Web:
Address: http://localhost:9095
First time login: admin
First time password: admin
Installation wizards¶
The Baculum API and the Baculum Web initial wizards help installing and connecting these two components together. In the Baculum Web wizard is added connection to the first API host called Main which is default API host for the Baculum Web.
To connect the Baculum Web to API part, you need to have at least one Baculum API instance with:
configured access to the Bacula Catalog database,
configured access to the Bacula console (
bconsole).
For the other API features as a capability to configure Bacula (with Bacula JSON tools) and component actions (start/stop/restart) they can be configured to provide the additional Baculum Web’s functions but it is not mandatory.
SUDO
To complete the Baculum API wizard, you may need to add sudo security policies
for bconsole, Bacula JSON tools and component actions. Inside the wizard you
will be able to get this sudo configuration adjusted to typed paths in wizard
fields. You can find it under Get sudo configuration links on the wizard
steps. Ready sudo configuration please write in a file in location:
/etc/sudoers.d/baculum-api
An example sudoers configuration for the Apache web server on CentOS/RHEL
may look like this:
Defaults:apache !requiretty
apache ALL = (root) NOPASSWD: /usr/sbin/bconsole
apache ALL = (root) NOPASSWD: /usr/sbin/bdirjson
apache ALL = (root) NOPASSWD: /usr/sbin/bsdjson
apache ALL = (root) NOPASSWD: /usr/sbin/bfdjson
apache ALL = (root) NOPASSWD: /usr/sbin/bbconsjson
apache ALL = (root) NOPASSWD: /usr/bin/systemctl start bacula-dir
apache ALL = (root) NOPASSWD: /usr/bin/systemctl stop bacula-dir
apache ALL = (root) NOPASSWD: /usr/bin/systemctl restart bacula-dir
apache ALL = (root) NOPASSWD: /usr/bin/systemctl start bacula-sd
apache ALL = (root) NOPASSWD: /usr/bin/systemctl stop bacula-sd
apache ALL = (root) NOPASSWD: /usr/bin/systemctl restart bacula-sd
apache ALL = (root) NOPASSWD: /usr/bin/systemctl start bacula-fd
apache ALL = (root) NOPASSWD: /usr/bin/systemctl stop bacula-fd
apache ALL = (root) NOPASSWD: /usr/bin/systemctl restart bacula-fd
Install using basic authentication method:
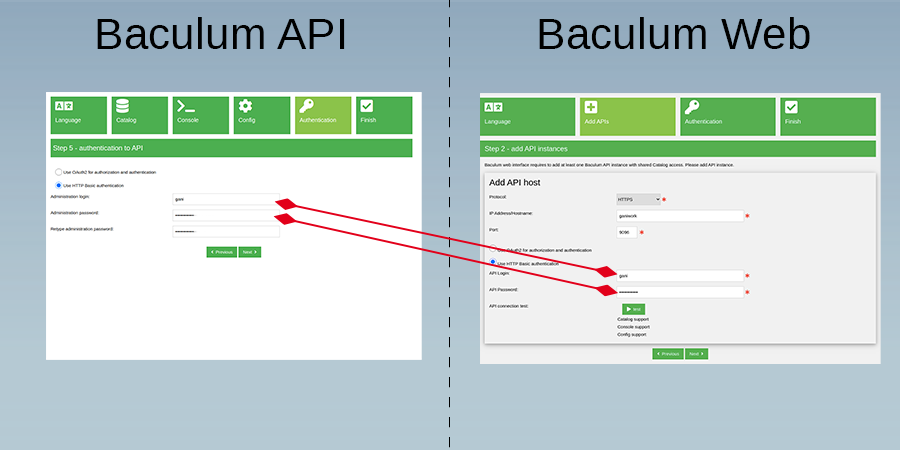
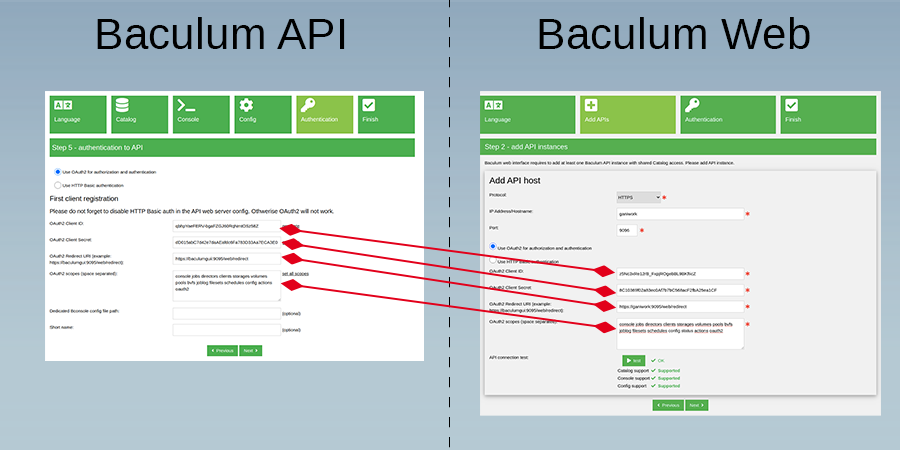
Install using OAuth2 authorization:
Authentication¶
Note
It is recommended to enable encrypted HTTPS connection with TLS certificates in the Baculum API and the Baculum Web web servers. When the connection is unencrypted, Baculum cannot guarantee security. The HTTP method in Baculum should only be used for testing purposes.
Baculum API¶
Basic
Basic is the only authentication method available in the Baculum API. It provides a simple and minimal way to access both API resources and API panel. This authentication can be configured on start in the initial Baculum configuration wizards.
Baculum Web¶
All authentication methods are available to setup on the Security page of the Baculum Web interface.
Basic
Basic is the default authentication method in the Baculum Web which is realized by web server. This authentication can be configured on start in the initial Baculum configuration wizards.
Local user
This type of authentication is realized by HTML form in the Baculum Web. Once this method is enabled, the web server basic authentication can be disabled.
LDAP
The Baculum Web can connect to the LDAP server to authenticate LDAP users. This method is realized by a HTML form in the Baculum Web. Once this method is enabled, the web server basic authentication can be disabled.
For the Baculum Apache web server configuration you can disable the basic authentication by changing the following configuration block:
# Apache 2.4
<IfModule mod_authz_core.c>
<Directory /usr/share/baculum/htdocs>
SetEnvIf Request_URI "^/web/redirect$" noauth=1
<RequireAny>
<RequireAll>
<RequireAny>
Require env noauth
Require env REDIRECT_noauth
</RequireAny>
Require all granted
</RequireAll>
<RequireAll>
AuthType Basic
AuthName "Baculum Auth"
AuthUserFile /usr/share/baculum/htdocs/protected/Web/Config/baculum.users
Require not env noauth
Require not env REDIRECT_noauth
Require valid-user
</RequireAll>
</RequireAny>
</Directory>
</IfModule>
into the following configuration block:
# Apache 2.4
<IfModule mod_authz_core.c>
<Directory /usr/share/baculum/htdocs>
Require all granted
</Directory>
</IfModule>
For the Baculum Lighttpd web server configuration the basic authentication can be disabled by removing the following configuration block:
$HTTP["url"] !~ "/web/redirect$" {
auth.backend = "htpasswd"
auth.backend.htpasswd.userfile = "/usr/share/baculum/htdocs/protected/Web/Config/baculum.users"
auth.require = ( "" => (
"method" => "basic",
"realm" => "Baculum Auth",
"require" => "valid-user"
)
)
}
Authorization¶
Note
It is recommended to enable encrypted HTTPS connection with TLS certificates in the Baculum API and the Baculum Web web servers. When the connection is unencrypted, Baculum cannot guarantee security. The HTTP method in Baculum should only be used for testing purposes.
OAuth2¶
General information¶
Baculum API
To obtain access tokens, the OAuth2 implementation in the Baculum API uses the Authorization Code Grant flow.
Authorization URL:
/oauth/authorizeAccess Token URL:
/oauth/token
Note
The Baculum API does not use refresh tokens. After expiration token the client application has to re-authorize again.
Authorization code expire time is 7 seconds, access token expire time is 1 hour. You can change these default values in the file:
/usr/share/baculum/htdocs/protected/Common/Class/OAuth2.php
You can find there the followin constants:
AUTHORIZATION_ID_EXPIRES_TIME,
ACCESS_TOKEN_EXPIRES_TIME.
To learn the Baculum API endpoints please visit the Baculum API documentation.
Baculum Web
OAuth2 callback URL (the redirect URI parameter) in the Baculum Web for
baculumgui host is following:
Enabling OAuth2¶
Default the Baculum API use the basic authentication. Enabling OAuth2 authorization gives additional features like:
access to Baculum API by secure tokens,
capability to assign dedicated Bconsole configuration files to OAuth2 accounts,
OAuth2 scopes to limit access to API endpoint by endpoint types (
/jobs/,/clients/… and so on).
Warning
In the Baculum API the basic authentication works both for API resources and for API panel. The OAuth2 authorization cannot work when the basic authentication for API resources is enabled. In this case the authentication only must be enabled for API panel, but not for API resources.
Before you start using OAuth2 in the Baculum API, first you must disable the web server basic authentication for the Baculum API resources but keep the authentication for the Baculum API panel as described below.
Apache web server
Please change in the Baculum Web configuration of the Apache web server
the Directory directive into the Location directive which indicates
on the /panel path.
In sample of the Baculum API web server configuration below please follow on instruction in comments:
#
# NOTE: When you use OAuth2 then change this Directory section
# From: <Directory /usr/share/baculum/htdocs>
# ...section body...
# </Directory>
# To: <Location /panel>
# ...section body...
# </Location>
#
<Directory /usr/share/baculum/htdocs>
#<Location /panel>
AuthType Basic
AuthName "Baculum Auth"
AuthUserFile /usr/share/baculum/htdocs/protected/API/Config/baculum.users
Require valid-user
#</Location>
</Directory>
Lighttpd web server
In sample of the Baculum API web server configuration please uncomment the two commented lines.
#
# Uncomment this line and closing braces below when you use OAuth2
#
#$HTTP["url"] =~ "^/panel.*$" {
auth.backend = "htpasswd"
auth.backend.htpasswd.userfile = "/usr/share/baculum/htdocs/protected/API/Config/baculum.users"
auth.require = ( "/" => (
"method" => "basic",
"realm" => "Baculum Auth",
"require" => "valid-user"
)
)
#}
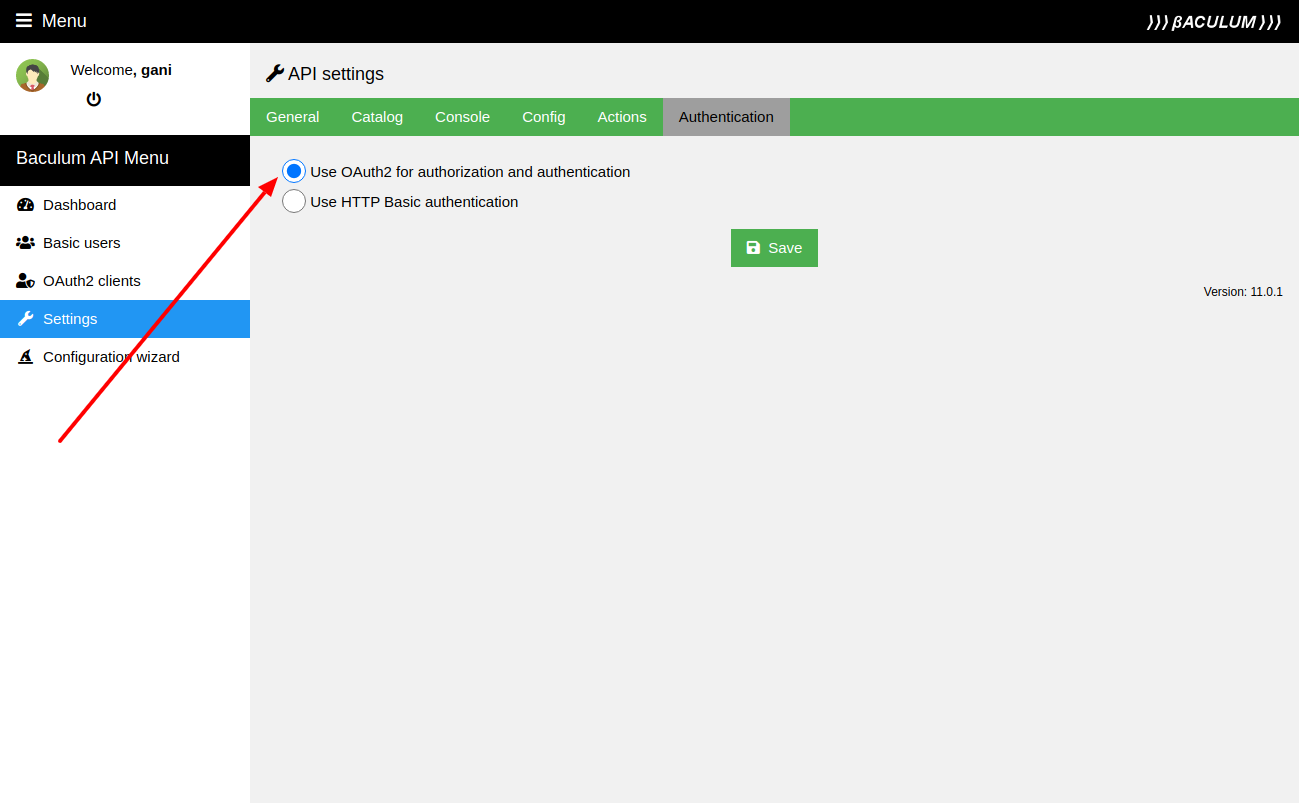
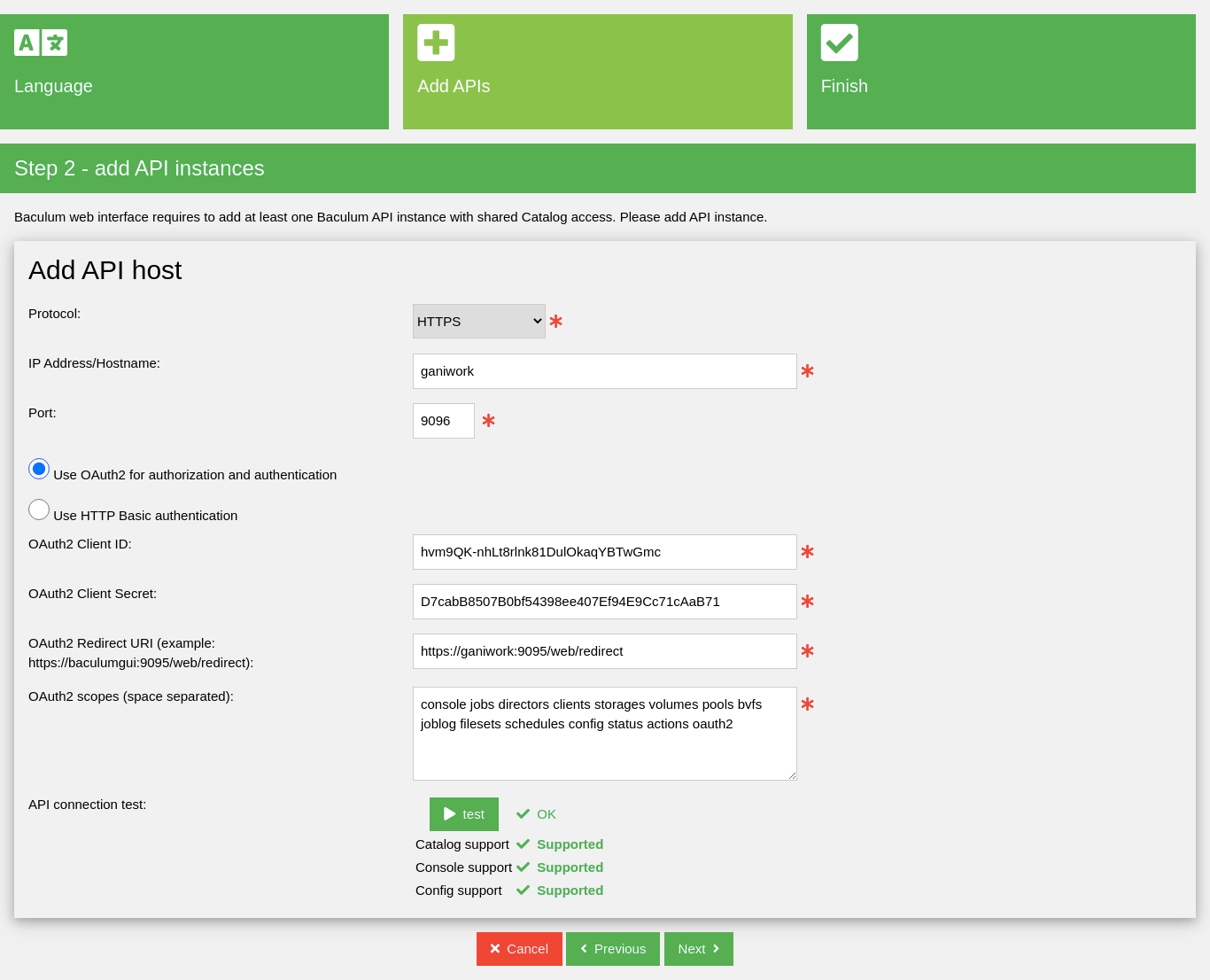
Enable OAuth2 in API
Once the basic authentication is changed in the web server configuration, now please switch the Baculum API into the OAuth2 mode. You can do it in a Baculum API configuration wizard as shown on the following image:
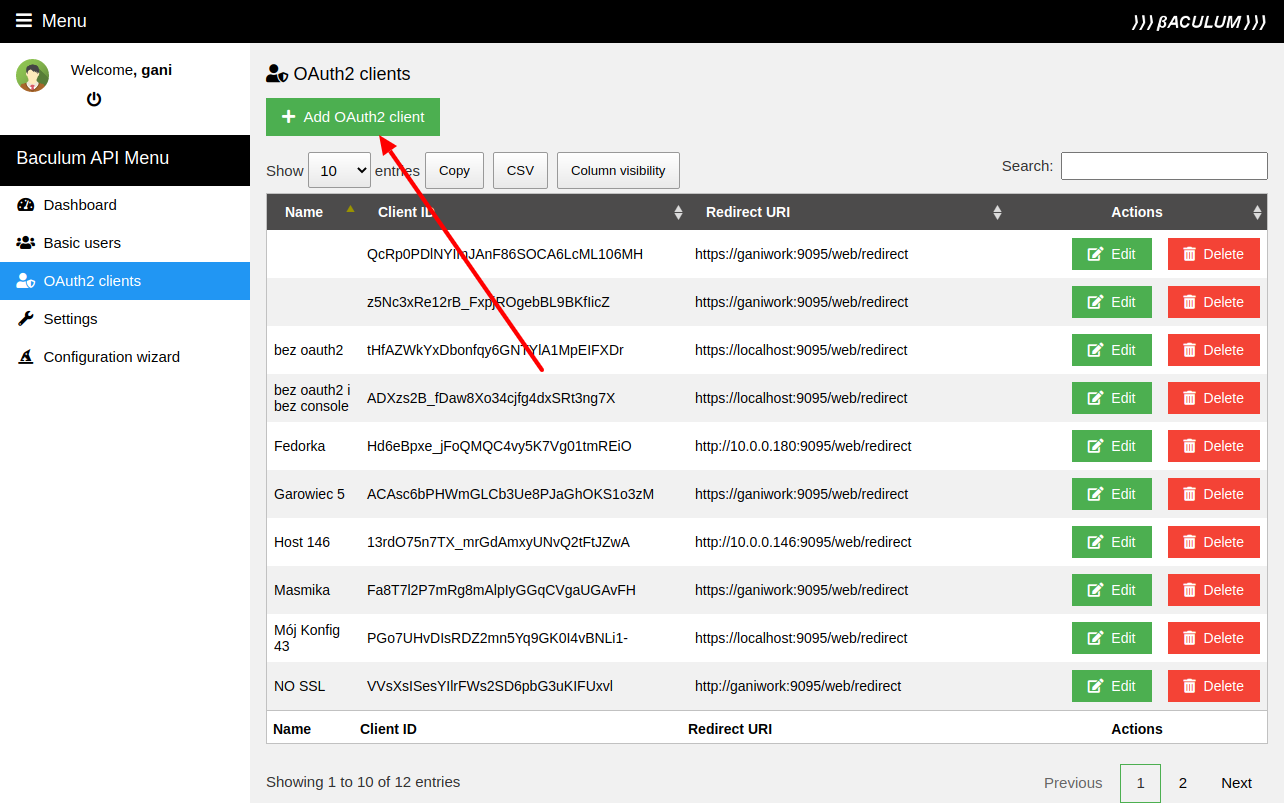
Create admin OAuth2 client params
You need to create the admin OAuth2 client account which will be used by the Baculum Web to connect to the Baculum API. You can create it in a Baculum API admin panel as shown on the following images:
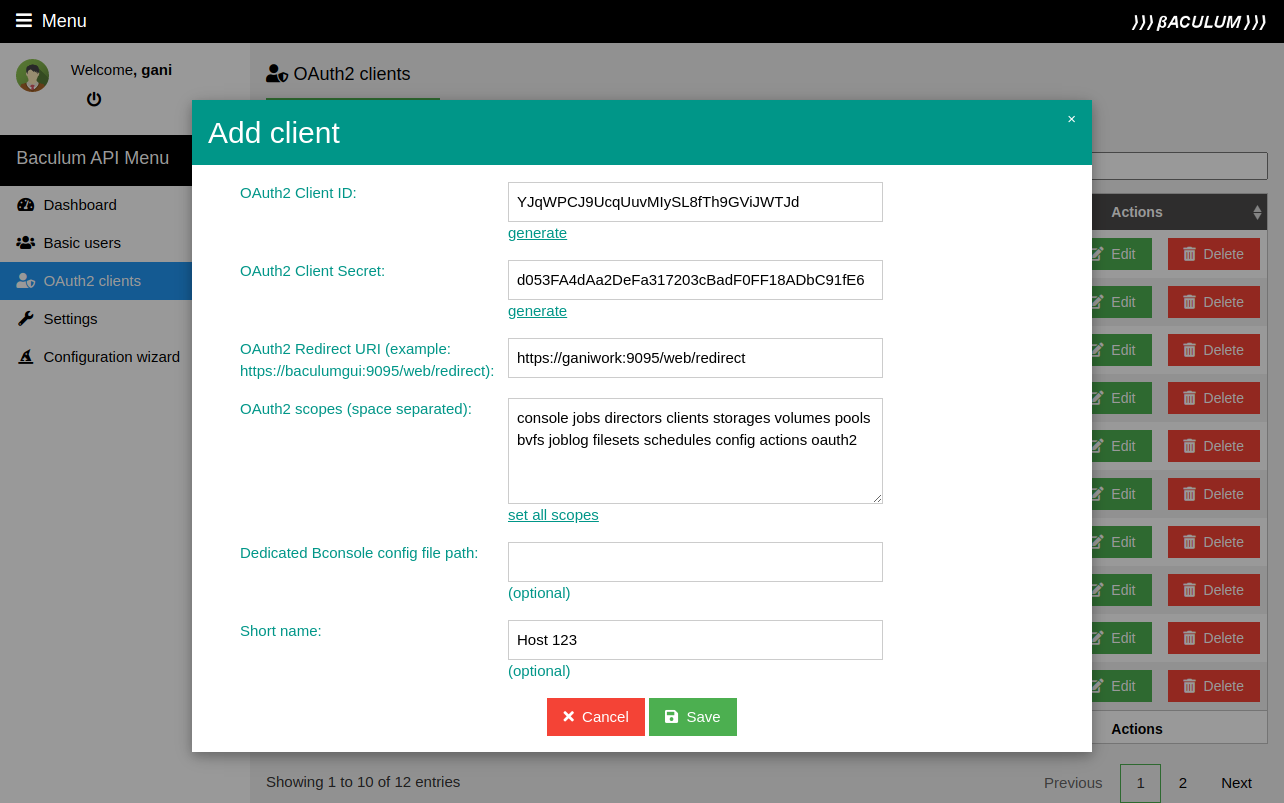
Connect Baculum Web using OAuth2 method
Now you can connect the Baculum Web to the Baculum API with using an OAuth2 authorization method in the Baculum Web configuration wizard.
OAuth2 video guide (Baculum version 9.6.7)
Users¶
The Baculum Web provides a multi-user interface that uses roles (RBAC - role-based access control) to determine available the Baculum Web pages for individual users. Both users and roles can be set on the Baculum Web Security page. More information about this function you can find in Access to pages chapter.
Besides of restricted pages access there is also possible to assign dedicated Bacula resources (jobs, clients, storages …etc.) to users. This way each user (or an user group) can access to restricted Bacula resources. This feature uses a Bacula Console ACL functions. To setup this type of restricted access, please follow the instructions in the video below. For more information, please visit Access to Bacula resources chapter.
Note
The example configuration shown in the video uses OAuth2. Before implementing it, please make sure, you have the OAuth2 authorization configured in Baculum API and Baculum Web. See the OAuth2 chapter.
Autochanger management¶
From Baculum version 11.0.2.1 there has been introduced support for
the autochanger management. It provides functions like:
load tape to tape drives
unload tape from tape drives
label tapes using barcodes
move tapes to import/export slots
release single import/export slot
release all import/export slots at once
update slots using barcodes
update slots by scanning tape labels written onto volume
To use it, please add autochanger device and tape drives to the Baculum API
using page named Devices. For using the autochanger management in Baculum
Web, Autochanger name in the Storage Daemon config must be the same as
autochanger name in Baculum API, as shown on image below.
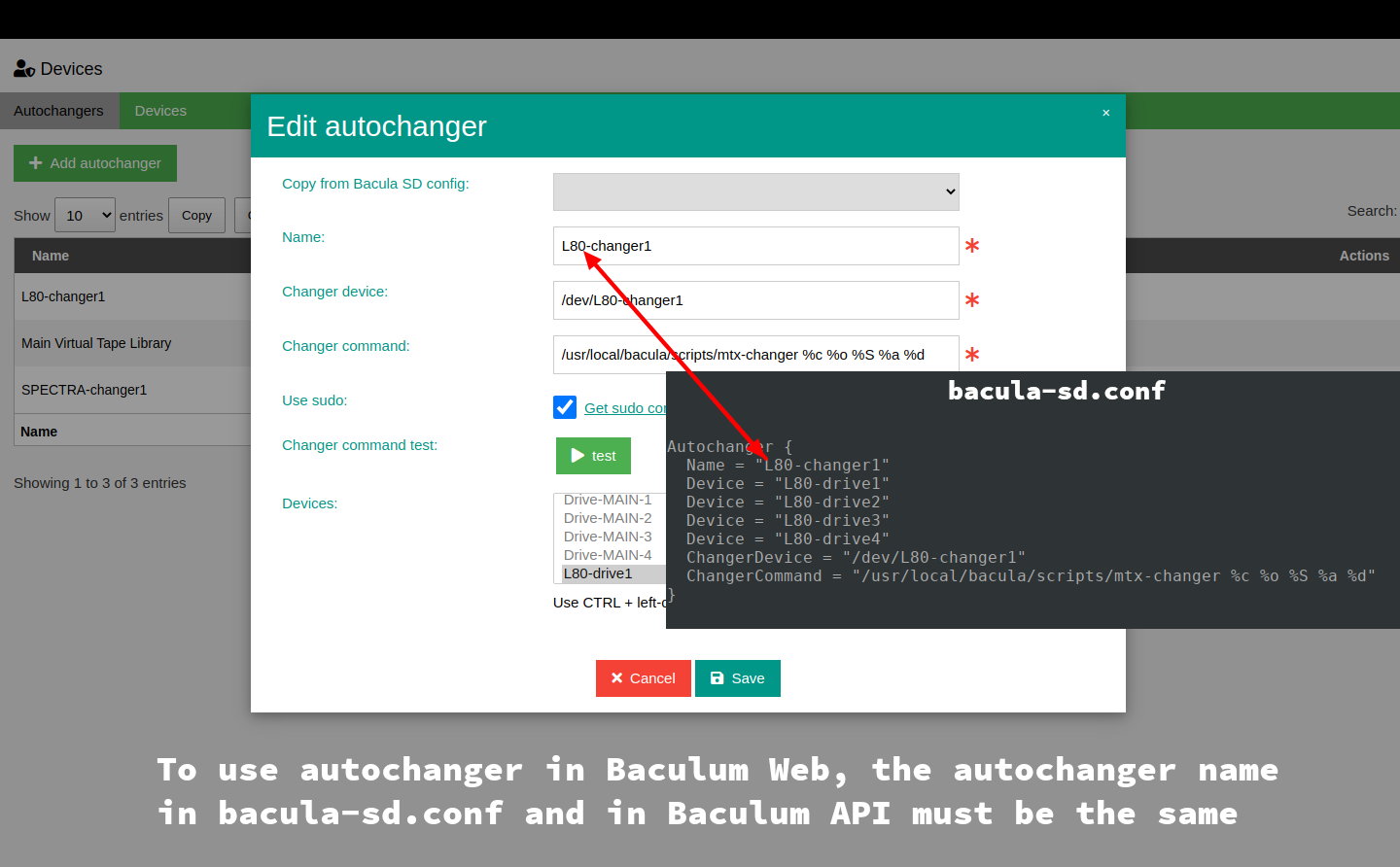
After adding autochanger and tape drives to Baculum API, on the Baculum Web
side please go to page Storage and select there the autochanger device.
Changer and drives management is available there on tab called Manage
autochanger.
Autochanger configuration video guide
Multiple API hosts¶
The Baculum Web is designed to work with API hosts. It can work with one API
host and with many API hosts. From version 11.0.2.2 there is also possible
to assign more API hosts than one to users. This way one user can manage his
own API hosts using the same Baculum Web interface.
On the figure below we can see example Baculum hosts topology with one Baculum Web and two Baculum API instances. One Baculum API can be used for regular administration work with backups, restores, clients and so on. The second one can be used for managing connected tape autochanger.
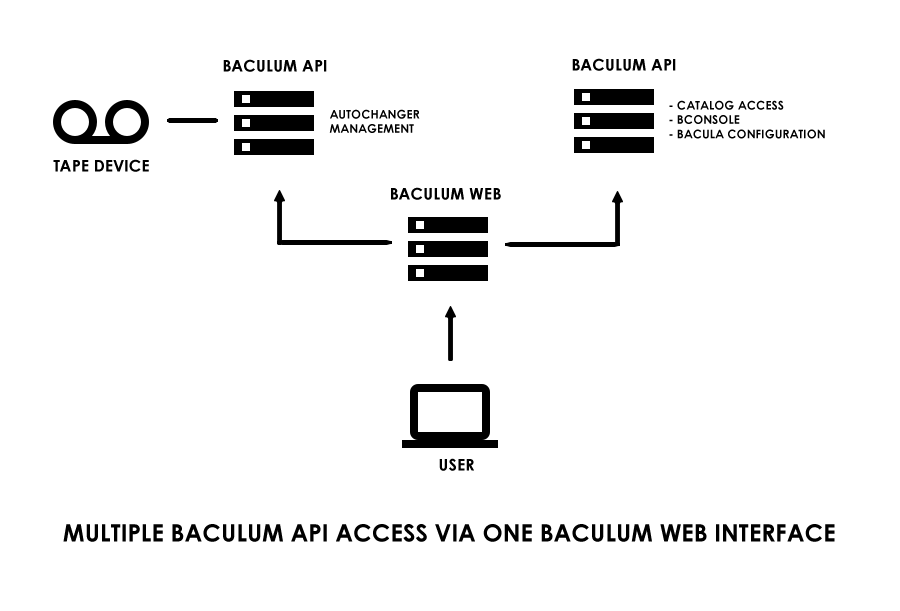
There can be many usages of multiple API hosts. You can use them for example for:
managing Bacula director, file daemon, storage daemon and console configuration on remote Bacula hosts,
working with multiple Bacula server instances,
managing Autochanger (slots, tapes, load, unload, move from/to import/export slots, label barcodes, update slots and others),
restarting remote Bacula components by Baculum API actions (start, stop, restart).
More information about working with multiple API hosts you can find in the Remote host management manual.
Multiple API hosts video guide
